I again had some fun this year playing KoreLogic's Crack Me If You Can password cracking contest at DEFCON 21. This year they separated teams between "Pros" and "Street" to make things a little more fair for individual users vs large groups. If you have any interest in password cracking then you can still download all the past 4 years of data and crack away! Huge thanks to the KoreLogic guys for putting on an excellent contest!
Of course my biggest problem is that by playing the game you don't get to really attend DEFCON so I didn't spend a lot of time cracking. You can tell my submissions were pretty much few and far between when I was back in my hotel room:
Even so I came in third place mostly because I spent a little extra time on Challenge 9 because of the point value - 250,000 points!
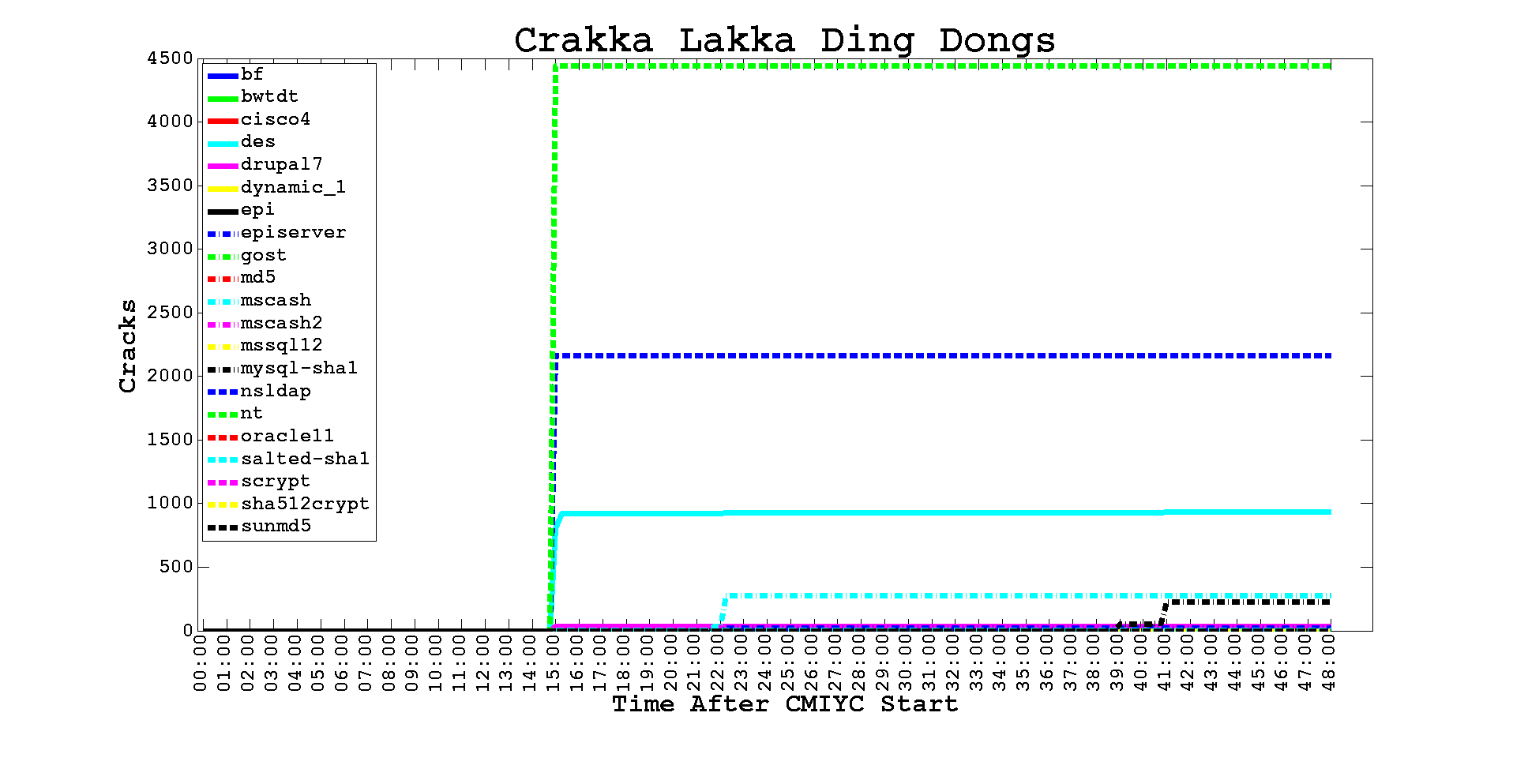
http://contest-2013.korelogic.com/stats_types.html:
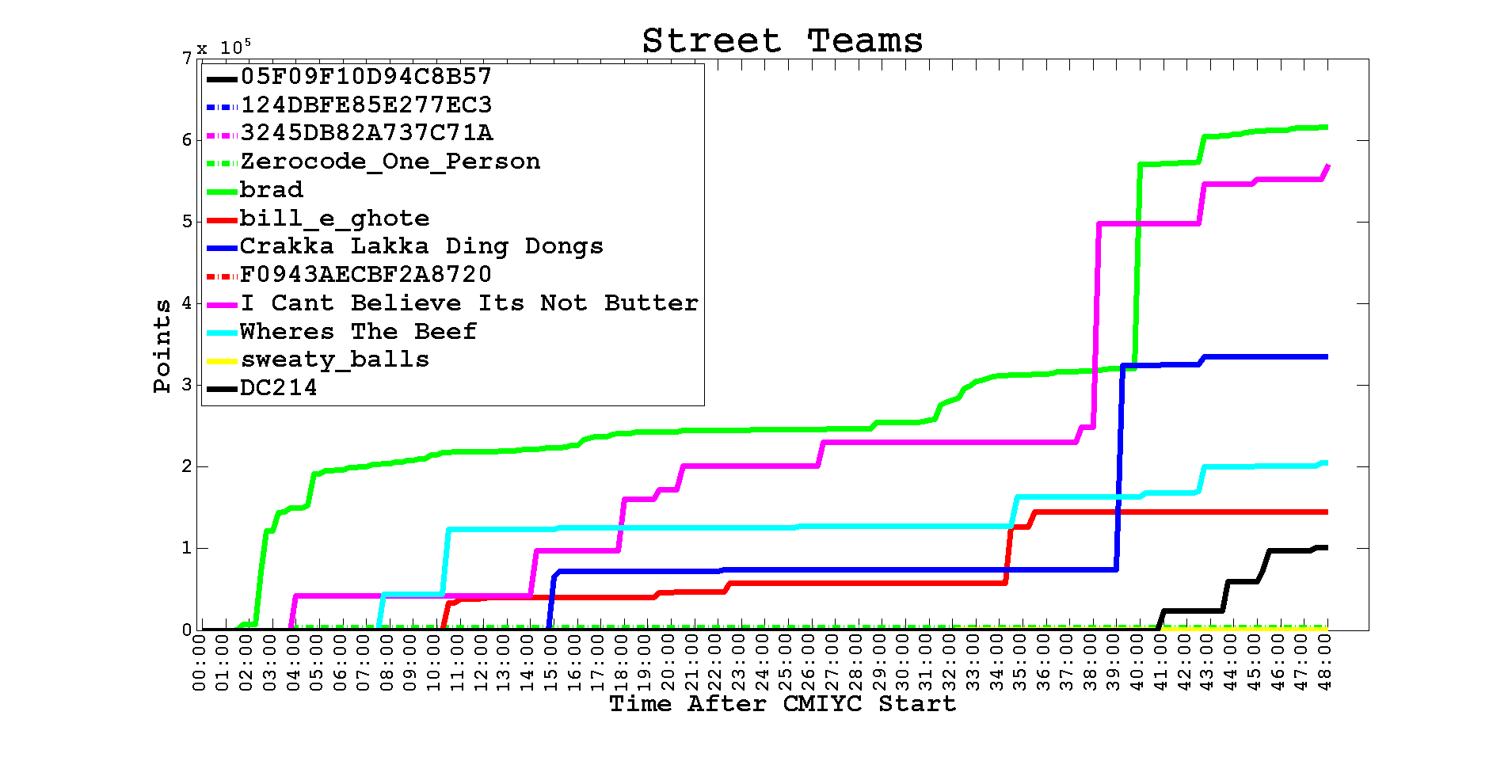
As you can tell from the graph the scores for three of us (brad, I Cant Believe Its Not Butter, and me) jumped near the final few hours of the contest because of Challenge 9. Here's how I did it...
Of course my biggest problem is that by playing the game you don't get to really attend DEFCON so I didn't spend a lot of time cracking. You can tell my submissions were pretty much few and far between when I was back in my hotel room:
Even so I came in third place mostly because I spent a little extra time on Challenge 9 because of the point value - 250,000 points!
http://contest-2013.korelogic.com/stats_types.html:
As you can tell from the graph the scores for three of us (brad, I Cant Believe Its Not Butter, and me) jumped near the final few hours of the contest because of Challenge 9. Here's how I did it...
Cracking Street Challenge 9
Challenge9 was delivered as a compressed tar file. After opening it up you're given a README and a dd-created filesystem:
In order to mount the file you need to skip the first 65536 bytes (1 cylinder) to get to the partition data. With the filesystem mounted lets check out what's in there!
Hmm, mabel.pfx looks interesting and the secret documents certainly are something we want to read. They should give us some information about Company3's password policy. But we can't read them because they're encrypted. Lets break the PFX file open using John The Ripper + jumbo from https://github.com/magnumripper/JohnTheRipper, the "pfx2john" tool and run it through the RockYou wordlist:
Success! Only took about 4 hours thanks to a weak password! Now we just have to figure out how to pull the files off, import the PFX into Windows... etc. etc.. Windows.. pffft.
1 comment:
Nice job mate!
Post a Comment