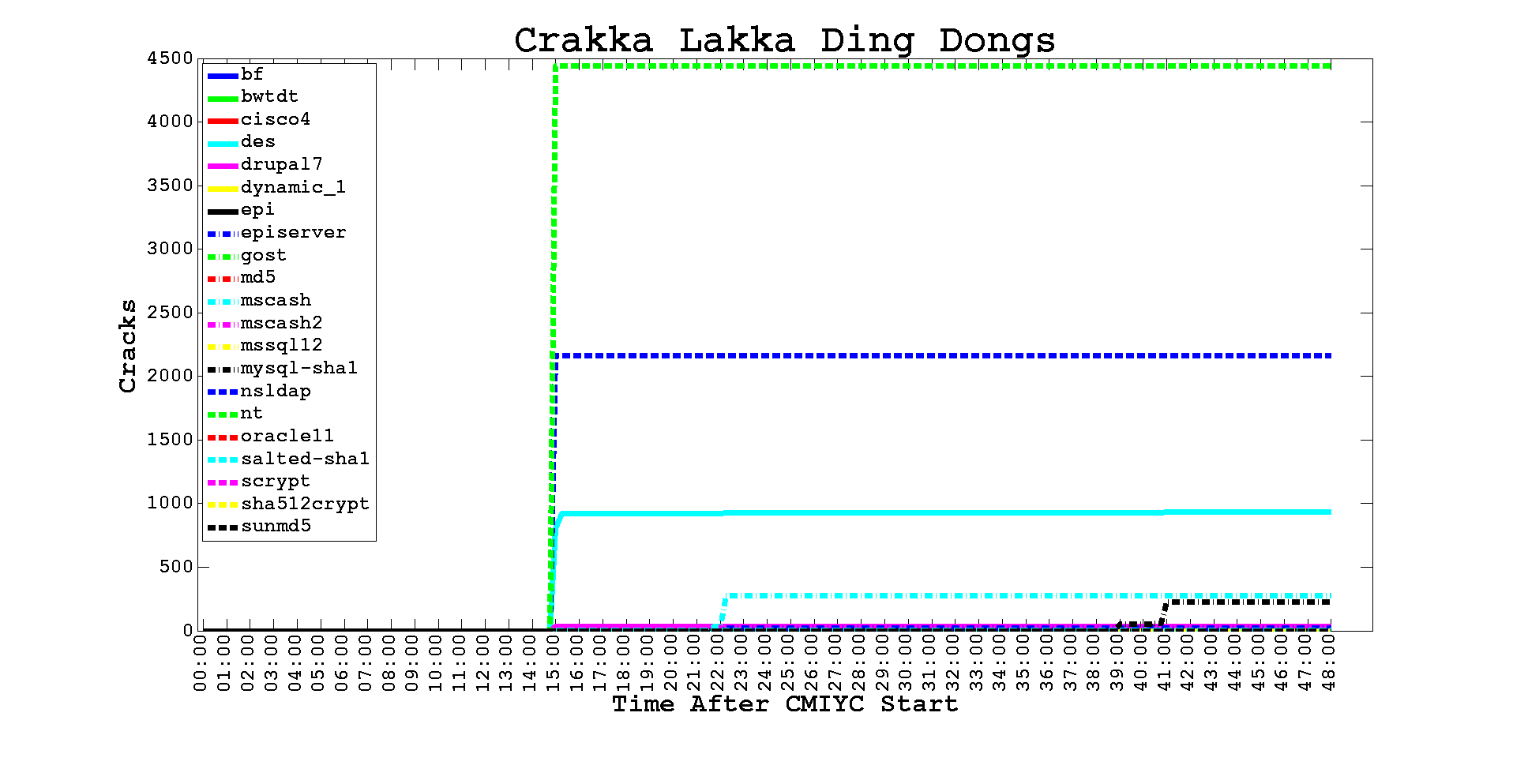
The Crack My If Can Street Challenge #3 was a fairly straight-forward "extract hashes and start cracking" problem. The hashes were Salted SHA1 inside a Berkeley DB. You could certainly have played with getting db_dump to work but it's just faster to use strings.
The internet is littered with wastes of space. This one is no different except that it is my waste of space.
Sunday, August 11, 2013
Crack Me If You Can 2013 - Challenge 9: Part 1
I again had some fun this year playing KoreLogic's Crack Me If You Can password cracking contest at DEFCON 21. This year they separated teams between "Pros" and "Street" to make things a little more fair for individual users vs large groups. If you have any interest in password cracking then you can still download all the past 4 years of data and crack away! Huge thanks to the KoreLogic guys for putting on an excellent contest!
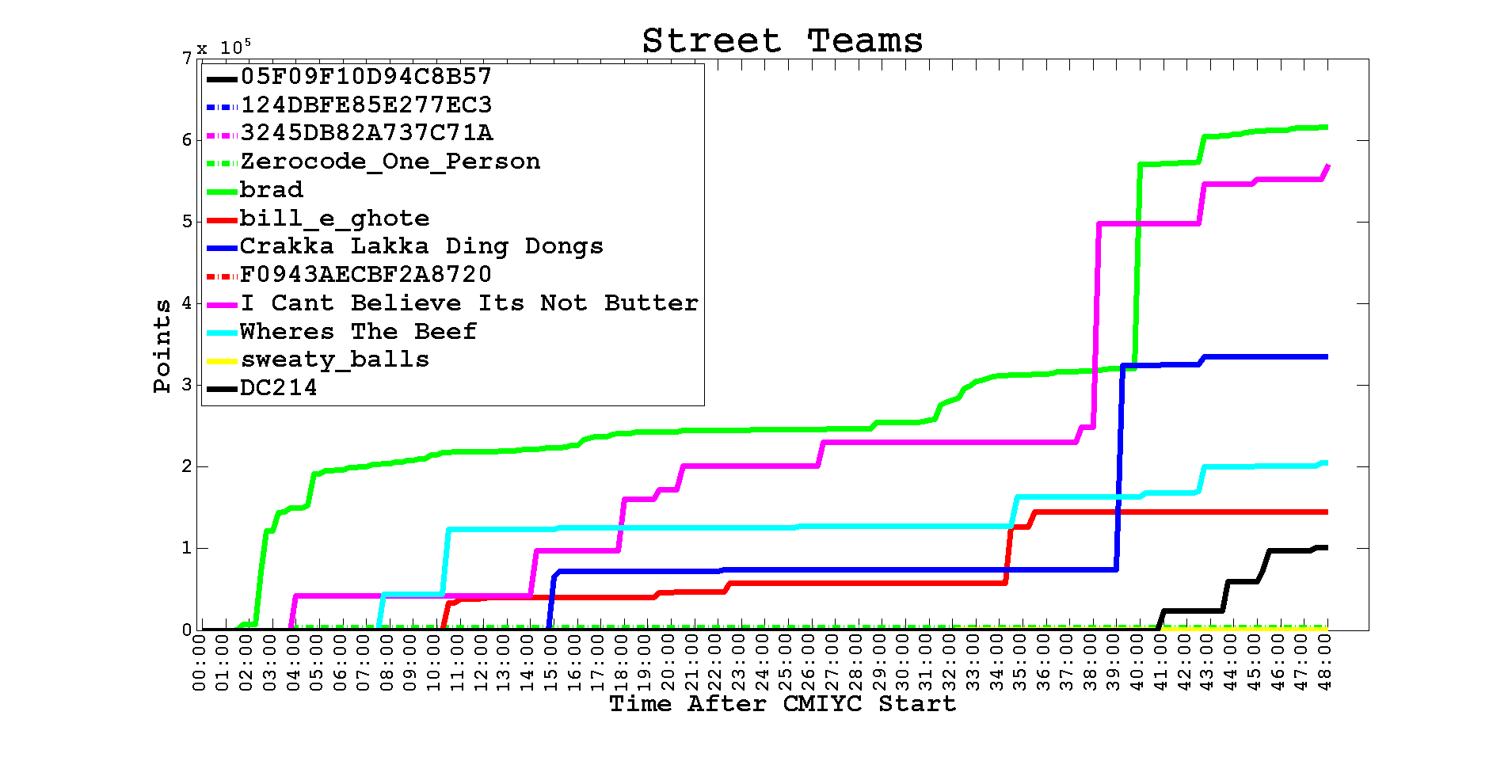
Of course my biggest problem is that by playing the game you don't get to really attend DEFCON so I didn't spend a lot of time cracking. You can tell my submissions were pretty much few and far between when I was back in my hotel room:
Even so I came in third place mostly because I spent a little extra time on Challenge 9 because of the point value - 250,000 points!
http://contest-2013.korelogic.com/stats_types.html:
As you can tell from the graph the scores for three of us (brad, I Cant Believe Its Not Butter, and me) jumped near the final few hours of the contest because of Challenge 9. Here's how I did it...
Of course my biggest problem is that by playing the game you don't get to really attend DEFCON so I didn't spend a lot of time cracking. You can tell my submissions were pretty much few and far between when I was back in my hotel room:
Even so I came in third place mostly because I spent a little extra time on Challenge 9 because of the point value - 250,000 points!
http://contest-2013.korelogic.com/stats_types.html:
As you can tell from the graph the scores for three of us (brad, I Cant Believe Its Not Butter, and me) jumped near the final few hours of the contest because of Challenge 9. Here's how I did it...
Subscribe to:
Posts (Atom)