HD Moore already did some great analysis on how the MS08-068 patch affected the SMB Relay attacks within Metasploit. The answer?
You can't attack the source workstation/server if MS08-068 has been applied.
This ONLY affects Squirtle if your evil agent attempts to communicate back to the victim. It should not impact attacking their IMAP, HTTP or File/Print servers.
As always the goal of Squirtle is to permit others to extend their own tools to permit the use of authentication requests from controlled browsers and at your own time or when the right users click on your evil link!
Have fun with the latest updates and thanks to Natron for pointing me towards HD's analysis.
The internet is littered with wastes of space. This one is no different except that it is my waste of space.
Saturday, November 15, 2008
Friday, November 14, 2008
Squirtle Updates: IMAP, Metasploit integration complete
I just gave a talk to everyone here at DeepSec 08. Other than the weather being a bit cold and wet Vienna is awesome. Everyone seems happy to be at this conference and to share and network with each other. It's always fun giving the Squirtle talk to new audiences and see their eyes light up as they start to get why this attack matters to their environments or how they could use it on a client's penetration test.
With the conclusion of this talk I'm happy to announce that two new evil agent updates have been completed!
On Nov 11th MSRC posted some information on MS08-068 implementing some changes to the NTLM protocol to neuter the SMB Relay attack and possibly (but not mentioned) Squirtle as well. I haven't had a chance to play with yet as I didn't want to possibly spoil the live demos so close to DeepSec. It's nearly time to spend the evening at Metalab so more information as it develops (I promise!)
Big thanks to everyone here at DeepSec for coordinating this one-of-kind conference. Vienna is such a beautiful place to visit, I only wish it would be earlier in the season when it's not so cold and dreary outside. I hope to come next year for DeepSec 09!
Also, look for my ugly mug to make an appearance on Help Net Security soon. It's a brief plea on using Squirtle and hopefully my excitement over reaching more people isn't too transparent. :)
With the conclusion of this talk I'm happy to announce that two new evil agent updates have been completed!
- IMAP Mirroring! Download a victim's entire IMAP directory! Use social engineering, have the help desk e-mail them a new password!
- Metasploit integration! SMB Relay an enterprise's server farm with Squirtle!
On Nov 11th MSRC posted some information on MS08-068 implementing some changes to the NTLM protocol to neuter the SMB Relay attack and possibly (but not mentioned) Squirtle as well. I haven't had a chance to play with yet as I didn't want to possibly spoil the live demos so close to DeepSec. It's nearly time to spend the evening at Metalab so more information as it develops (I promise!)
Big thanks to everyone here at DeepSec for coordinating this one-of-kind conference. Vienna is such a beautiful place to visit, I only wish it would be earlier in the season when it's not so cold and dreary outside. I hope to come next year for DeepSec 09!
Also, look for my ugly mug to make an appearance on Help Net Security soon. It's a brief plea on using Squirtle and hopefully my excitement over reaching more people isn't too transparent. :)
Tuesday, September 02, 2008
Upcoming Speaking Gigs
Tying a neat little bow to my NTLM/HTTP research I'll be presenting "One XSS to Rule The Enterprise" at ToorCon X the end of September and "NTLM SSO Weaknesses" at DeepSec in November. Both talks will show off the Squirtle Attack Toolkit. Hopefully I'll have some of the updates I didn't get into the DefCon release ready by ToorCon!
When friends ask "should I go to Defcon?" I always respond "Hey, check out ToorCon. It's in a nicer climate!" Vegas in July? Pfft, San Diego in September! One of the best conventions out there, period. Just check out the conference lineup!
When friends ask "should I go to Defcon?" I always respond "Hey, check out ToorCon. It's in a nicer climate!" Vegas in July? Pfft, San Diego in September! One of the best conventions out there, period. Just check out the conference lineup!
Tuesday, August 12, 2008
Passing The Dutchie @ Defcon 16
Like many things with this blog, I don't prioritize it above things like hanging out with my girlfriend, going to work, sleeping, breaking my iPhone, losing all my Defcon pictures, etc.
 Last weekend was Defcon 16. I had a really great time speaking to a packed house on the death of NTLM. Slides, slide video and source code to Squirtle are now available for your pleasure. I'll be doing some more work and documentation on Squirtle shortly.
Last weekend was Defcon 16. I had a really great time speaking to a packed house on the death of NTLM. Slides, slide video and source code to Squirtle are now available for your pleasure. I'll be doing some more work and documentation on Squirtle shortly.
A few quick changes were made to the slide deck from what was presented (and the slides on the CD are waaaaaay something different :). Mostly added NTLM Signing as a mitigation and correctly stating that JoMoKun did the Samba Pass-The-Hash modifications. Sorry!
More updates coming.
 Last weekend was Defcon 16. I had a really great time speaking to a packed house on the death of NTLM. Slides, slide video and source code to Squirtle are now available for your pleasure. I'll be doing some more work and documentation on Squirtle shortly.
Last weekend was Defcon 16. I had a really great time speaking to a packed house on the death of NTLM. Slides, slide video and source code to Squirtle are now available for your pleasure. I'll be doing some more work and documentation on Squirtle shortly.A few quick changes were made to the slide deck from what was presented (and the slides on the CD are waaaaaay something different :). Mostly added NTLM Signing as a mitigation and correctly stating that JoMoKun did the Samba Pass-The-Hash modifications. Sorry!
More updates coming.
Thursday, August 07, 2008
NTLM is Dead: Defcon 16
Wednesday, July 30, 2008
Attacking NTLM
Defcon presentation times have been confirmed for a few weeks now and I've been slaving away at my slides and source code for a while now. I gave a pre-talk at work the other day and have decided to redo a lot of the slides. That's what you get when you ask for slides 38 days before the presentation. :)
Of course I'll have the full slides on-line after the conference but if you're coming to Defcon please come to my talk: Friday, August 8th at 2pm.
What exactly will I be talking about? Well, it's really difficult to describe succinctly but the best way I can say it is: An XSS inside your company == Total Domain Ownage.
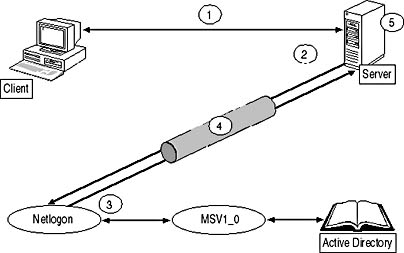
Was that a scoff I just heard under your breath? Honestly, I'm not lying here. Because of the way NTLM and Windows Single Sign-On works your run-of-the-mill cross site scripting error on an internal resource can DEVASTATE your enterprise!
Stay tuned.
Of course I'll have the full slides on-line after the conference but if you're coming to Defcon please come to my talk: Friday, August 8th at 2pm.
What exactly will I be talking about? Well, it's really difficult to describe succinctly but the best way I can say it is: An XSS inside your company == Total Domain Ownage.

Was that a scoff I just heard under your breath? Honestly, I'm not lying here. Because of the way NTLM and Windows Single Sign-On works your run-of-the-mill cross site scripting error on an internal resource can DEVASTATE your enterprise!
Stay tuned.
Friday, June 13, 2008
MS Cache and John the Ripper
Chalk this one up to knowledge remembered, forgotten, and then remembered again!
Lately I have been playing with using our MPI John the Ripper cluster to increase the crack rate of MS Cache passwords. With a very long list of passwords, some of which I knew would be easy to crack, I set out and started the process on 20 nodes. After a few days and ZERO cracks I started to wonder what the hell was going on.
The answer is one I knew many years ago when cachedump first came on the scene. The MS Cache encryption routine's salt includes the lower case username as part of the salt! Because some of the cachedump tools take the username out of the registry as-is and don't convert the case you'll run JTR for days with an invalid salt. No cracks for you!
So we can do a couple of things here:
John The Ripper's source code is really easy to fix and the quickest to do so a simple diff against mscash_fmt.c:
And now I don't have to remember this every time! JTR will remember for me and with a cluster of 20 nodes all running around 600,000 cracks a second maybe SOMETHING will crack. :)
Lately I have been playing with using our MPI John the Ripper cluster to increase the crack rate of MS Cache passwords. With a very long list of passwords, some of which I knew would be easy to crack, I set out and started the process on 20 nodes. After a few days and ZERO cracks I started to wonder what the hell was going on.
The answer is one I knew many years ago when cachedump first came on the scene. The MS Cache encryption routine's salt includes the lower case username as part of the salt! Because some of the cachedump tools take the username out of the registry as-is and don't convert the case you'll run JTR for days with an invalid salt. No cracks for you!
So we can do a couple of things here:
- Remember this next time and manually lowercase the usernames
- Tell the authors to modify the tools we use to grab the cache hashes
- Patch the tools ourselves (if we have the sources) and give them to the author
- Modify the cracking program to always lowercase the usernames
John The Ripper's source code is really easy to fix and the quickest to do so a simple diff against mscash_fmt.c:
--- mscash_fmt.c 2008-06-13 15:56:07.000000000 -0700
+++ mscash_fmt-lower.c 2008-06-13 15:55:49.000000000 -0700
@@ -16,6 +16,7 @@
*/
#include
+#include
#include "arch.h"
#include "misc.h"
@@ -158,6 +159,9 @@
l = strlen(ciphertext);
strncpy(out, ciphertext + 2, l - PLAINTEXT_LENGTH + 1);
+ for(l=0; l < strlen(out); l++) {
+ out[l] = tolower(out[l]);
+ }
return out;
}
And now I don't have to remember this every time! JTR will remember for me and with a cluster of 20 nodes all running around 600,000 cracks a second maybe SOMETHING will crack. :)
Friday, June 06, 2008
NTLM, DefCon and Java!
John Heasman just posted a rocking method of obtaining NTLM hashes out of an enterprise by turning a Java applet into a web server! Check it out!
This year I'll be presenting at DefCon on the history of NTLM attacks, how they work and why we need to get rid of it. I'll release a tool that will combine as many hacks as I can get working to use captured users and their authentication tokens. There's been a lot of talk in the past few years about browser security and it's mostly hinged around using Javascript as a port scanner, sending attacks through the browser, attacking the platforms, etc. Few have been talking about an Enterprise-class risk and since that's what I get paid to think about I'm gonna blow it open. :) Come to DefCon and have a great time!
SyScan was great, a little small but helpful to bring the confidence up speaking to people who have no clue who I am! I learned quite a bit about my speaking style which helped firm up ideas about the DefCon presentation. I presented a combination of Web Security Mistakes including how to get a free MacWorld pass and spoke more about the future of PokeHashBall.
We stayed a few extra days to soak up the culture and soak the sweat into our clothes some more since this was our first trip to Hong Kong. The MongKok Computer Center was interesting but didn't seem to really have the deals I was expecting. I didn't get to any of the other computer centers however. Maybe next trip!
We went through Narita airport on the way back so I stopped at Duty Free and bought a bottle of Suntory Whiskey, the kind Bill Murray is hawking in the movie "Lost In Translation". For relaxing times, make it Santory time. . .
They have some of the greatest commercials.
This year I'll be presenting at DefCon on the history of NTLM attacks, how they work and why we need to get rid of it. I'll release a tool that will combine as many hacks as I can get working to use captured users and their authentication tokens. There's been a lot of talk in the past few years about browser security and it's mostly hinged around using Javascript as a port scanner, sending attacks through the browser, attacking the platforms, etc. Few have been talking about an Enterprise-class risk and since that's what I get paid to think about I'm gonna blow it open. :) Come to DefCon and have a great time!
SyScan was great, a little small but helpful to bring the confidence up speaking to people who have no clue who I am! I learned quite a bit about my speaking style which helped firm up ideas about the DefCon presentation. I presented a combination of Web Security Mistakes including how to get a free MacWorld pass and spoke more about the future of PokeHashBall.
We stayed a few extra days to soak up the culture and soak the sweat into our clothes some more since this was our first trip to Hong Kong. The MongKok Computer Center was interesting but didn't seem to really have the deals I was expecting. I didn't get to any of the other computer centers however. Maybe next trip!
We went through Narita airport on the way back so I stopped at Duty Free and bought a bottle of Suntory Whiskey, the kind Bill Murray is hawking in the movie "Lost In Translation". For relaxing times, make it Santory time. . .
They have some of the greatest commercials.
Monday, May 26, 2008
Heading to SyScan Hong Kong

I've been given the opportunity to talk about Web Security at this year's SyScan conference in Hong Kong. This is my first trip to Asia so I'm really really excited about it! I haven't traveled much outside of North America -- the trip to Chaos Camp was my first oceanic flight. The Pacific Ocean is so huge that our flight from SFO will total 17 hours! It was only 9 hours to Dusseldorf!
This talk will expand on my OWASP talk on trusting the client and the MacWorld Pass hack. I'll also give a brief bit on NTLM Single Signon (NTLMSSP) attacks. Looking forward and will update at the con!
Friday, February 22, 2008
Your Client-Side Security Sucks
Last night I presented at the local OWASP chapter titled "Your Client-Side Security Sucks: STOP USING IT (as your only method of security)" and the turn-out was great. I met some really awesome people and the subject matter, while not cutting-edge research, appeared to hit home.
We, as Web Application people, are still making some simple mistakes. This presentation highlighted three REAL WORLD examples of client-side security done incorrectly.
The PDF slides are available here and soon I'll have a QuickTime video with a voiceover. I LOOOOOVE Keynote now! It has such useless transformations that you must pull back or else the content will be lost. How awesome is that? Plus exporting to a QuickTime so others can enjoy your ego-boosting flame build-in!
Rumor has it there will be an OWASP regional conference in the near future so hopefully I'll present this again with some improved slides and other real world examples. If you have any examples but don't want to "go public" yourself, let me know and I'll share them. This is one of the first things you're supposed to learn as a web developer so I have no problem exposing others. JavaScript, Java and Flash do not equate to protection! Shoot me an e-mail.
The second presenter, as luck would have it, is working on a tool exactly like I had done for NTLM relay attacks! We had a good chat about where we both saw our tools going in the future. It has renewed my energy in completing the PokeHashBall tools
at least. Thanks, eric!
We, as Web Application people, are still making some simple mistakes. This presentation highlighted three REAL WORLD examples of client-side security done incorrectly.
The PDF slides are available here and soon I'll have a QuickTime video with a voiceover. I LOOOOOVE Keynote now! It has such useless transformations that you must pull back or else the content will be lost. How awesome is that? Plus exporting to a QuickTime so others can enjoy your ego-boosting flame build-in!
Rumor has it there will be an OWASP regional conference in the near future so hopefully I'll present this again with some improved slides and other real world examples. If you have any examples but don't want to "go public" yourself, let me know and I'll share them. This is one of the first things you're supposed to learn as a web developer so I have no problem exposing others. JavaScript, Java and Flash do not equate to protection! Shoot me an e-mail.
The second presenter, as luck would have it, is working on a tool exactly like I had done for NTLM relay attacks! We had a good chat about where we both saw our tools going in the future. It has renewed my energy in completing the PokeHashBall tools
at least. Thanks, eric!
Thursday, January 24, 2008
I Like Apple Products But I Am Not A MacHead
Some have asked that because I've pick on MacWorld am I a MacHead? The answer is no, but I do like Apple products. This will be a fun movie to see as there certainly is a cult of Mac, especially here in the Bay Area.
Monday, January 14, 2008
Another Free MacWorld Platinum Pass? Yes in 2008!

Last year at this time I disclosed an issue with the IDG/MacWorld Expo registration that allowed people Free Platinum Passes (valued at $1,695). I communicated this issue with IDG the week of MacWorld and they removed all the codes, fixed the site, and said thanks. Questions were asked on how to write better code and I gave them a few tips (don't trust user input, don't give your secret codes to everyone, encryption is not one-way, etc). Did they listen?
Nope.
Who wants to stand in line to see the Steve Jobs keynote at MacWorld? I mean have you SEEN the lines there? Really? I want to know WHATS IN THE AIR(tm)!!!
Honestly it's academic to me. I didn't even go to the keynote. :P
Getting Your Golden (Well, Blue) Ticket:
This year the cost of Platinum Passes has gone up to $1,895. That's a lot of money but you get a lot of cool things:
- A free lunch every day
- Free ticket to the MacWorld Blast
- Seminars (MacWorld is more than just the keynote and Expo)
- Priority Access Line to the Keynote
Like last year IDG is passing a long list of MD5 hashes to the client browser and validating them in JavaScript before sending a request to the server -- but that's really only a problem if the codes that give the discounts exist and are easily cracked. Lets see if we can get lucky this year.
Obtaining the codes -- Same as last year:
Step 1. Navigate to the main registration page
Step 2. Submit your initial data and view the source of the main registration page, search for "Priority Code"
Step 3. See the JavaScript "onchange" function? It's calling "check_password()"
Step 4. Search for "check_password()" and you'll find the list of valid codes in MD5
Step 5. Format the data for your cracker of choice and start cracking!
Cracking the codes:
I like John The Ripper for all my hash cracking needs. It's flexible, easy to use and affordable! There are two main methods used to crack passwords in John, using a wordlist or incrementing through a given keyspace. I always begin with a wordlist run just to kick out the quickies. The hash for "NONE" breaks but we already know that doesn't do anything for us.
Incremental mode is our next step but we know lower case letters aren't used so a quick look at the configuration file shows an external mode "Filter_LanMan" that throws everything to upper case. A quick run through doesn't net any cracked hashes unfortunately. There are still over 1,000 hashes to crack so we have to be a bit more intelligent in our cracking (or throw more machines, wait longer, get a PS3, etc).
A Brief Cracking Sidebar:
Incremental cracking can take a long time to perform. The size of your keyspace (k) and the maximum word length (l) determine the total number of permutations that have to be encrypted to check every instance (P). P=k^l. Take the benchmark cracks-per-second your machine takes (Cs), do the math (P/Cs) and you have the number of seconds it takes to run an Incremental.
For example lets make k = 69, l = 8 and Cs = 30 million:
((69^8)/30M) / 60 = 285,443.54 minutes (3.68 months!)Changing l for different lengths and the time changes accordingly:
((69^7)/30M) / 60 = 4,136.86 minutes for 7 charsand so on. . . The time is cumulative and those are just my numbers. Some have found ways to increase the speed to 1 billion cracks-per-second. Until that code is released or we write our own, we have to work with clusters of machines to reach that. My little cluster of 9 nodes can do just about 60 million MD5's a second so a full 8 character run would take nearly 2 months to complete.
((69^6)/30M) / 60 = 59.95 minutes for 6 chars
Now that you know the math and the big mountain ahead of us, how can we get on the gondola that takes you over half of it without much effort? The answer is simple, vendor codes and keyword masking!
Vendors receive a group of codes each to pass along to their customers, potential customers, friends, family, etc. These typically provide free Expo access but maybe they'll help trim down this mountain to something manageable. These free codes get passed around like candy so finding one takes a few Google searches. 08-G-PC189, 08-G-PC178, 08-G-PC260,
Time To Build An External Filter:
Now that we have a mask (08-x-y(n)) time to modify the john.conf accordingly:
With that, we run and wait...[Incremental:MW]
File = $JOHN/lanman.chr
MinLen = 6
MaxLen = 6
CharCount = 69
[List.External:MW]
void filter()
{
int i, c;
i = 0;
while (c = word[i]) {
// If character is lower case, convert to upper
if (c >= 'a' && c <= 'z')
word[i] &= 0xDF;
i++;
}
// We know the static filter 08-?-?????
// Add or remove word[]s to fit the incremental length
word[9] = word[5];
word[8] = word[4];
word[7] = word[3];
word[6] = word[2];
word[5] = word[1];
word[4] = '-';
word[3] = word[0];
word[2] = '-';
word[1] = '8';
word[0] = '0';
}
# john -i=MW -e=MW mw2k8.codes --format=raw-MD5.. but not too long because the first code looks REALLY interesting: 08-S-STAFF. Lets try it!
Loaded 1341 password hashes with no different salts (Raw MD5 [raw-md5 SSE2])
Download the High Quality version.
Voila. For the second year in a row, a free Platinum Pass in less than a day.
On January 7th we noticed the MD5 hashes changed in the source code. While the special code was still listed it no longer gave a 100% discount when entered. Some codes still provide a small percentage discount and a few do provide a free expo pass. We still have 14 codes left to crack so no telling if those are any good. :)
Thanks to Josh Bernstein and Garrett Gee for reminding me MacWorld was coming up and independently confirming these findings.
Maybe next year the problem will be fixed? Anyone in a betting mood? :)
Subscribe to:
Posts (Atom)
